ActiveShareFS 2010 Configuration
There are several ways to allow access to your webapp after installing ActiveShareFS. The following illustrates basic ideas. For full configuration options, see here.
Allow a user access via User Policy in Central Administration
First, configure the asfs.xml like the following:
<serverVariables>
<serverVariable id="uid" name="HTTP_UID"/>
</serverVariables>
<accounts>
<account>
<username value="$uid$"/>
</account>
</accounts>
The above will simply use the HTTP_UID as the SharePoint account name for all users logging in. If your admin has a uid of value “someadmin”, you would add a user via User Policy for the webapp with “smp:someadmin”:
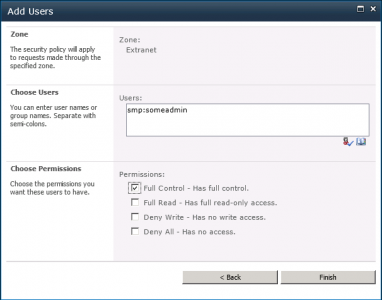
This user will gain Full Control permissions when they access the webapp.
Allow a user as Site Collection Administrator
Ensure you have a working asfs.xml configuration like the User Policy example above.

This method requires that the roles already exist in the site collection with either their own permissions or added to existing SharePoint security groups. For example, if a SharePoint security group “Site Visitors” has the Read permission, and a role called “srp:visitor” is added to that group, the following asfs.xml will give all users the Read permission.
<serverVariables>
<serverVariable id="uid" name="HTTP_UID"/>
</serverVariables>
<accounts>
<account>
<username value="$uid$"/>
</account>
</accounts>
<roles>
<role value="visitor"/>
</roles>
If you have an attribute that contains role-like information, you could do something like this:
<serverVariables>
<serverVariable id="uid" name="HTTP_UID"/>
<serverVariables id="unscopedaffiliation" name="HTTP_UNSCOPEDAFFILIATION"/>
</serverVariables>
<accounts>
<account>
<username value="$uid$"/>
</account>
</accounts>
<roles>
<role value="$unscopedaffiliation$"/>
</roles>
The above would map the multi-valued unscopedaffiliation attribute for all users. If a user’s unscopedaffiliation had the values “student” and “visitor”, the user would access SharePoint with roles “student” and “visitor”. If a SharePoint group contained a member named “srp:visitor”, then the user would gain the permissions of that SharePoint group.
Configure access via on-the-fly mapping to SharePoint security groups
You can also configure ActiveShareFS to add users to SharePoint groups directly, on-the-fly.
<serverVariables>
<serverVariable id="uid" name="HTTP_UID"/>
<serverVariable id="unscopedaffiliation" name="HTTP_UNSCOPEDAFFILIATION"/>
</serverVariables>
<conditions>
<condition id="students">
unscopedaffiliation=="student"
</condition>
</conditions>
<accounts>
<account>
<username value="$uid$"/>
</account>
</accounts>
<groups>
<group conditionId="students" relativeUrl="/" name="Site Students"/>
<group relativeUrl="/" name="Site Visitors"/>
</groups>
The above will add users with “student” in their unscopedaffiliation attribute to SharePoint group “Site Students”. Additionally, all users will be added to “Site Visitors” (no conditionId). Check out the full documentation on the asfs.xml configuration file.
